What Is A Intercept? The Hidden Switch That Controls Network Traffic Flow
What Is A Intercept? The Hidden Switch That Controls Network Traffic Flow
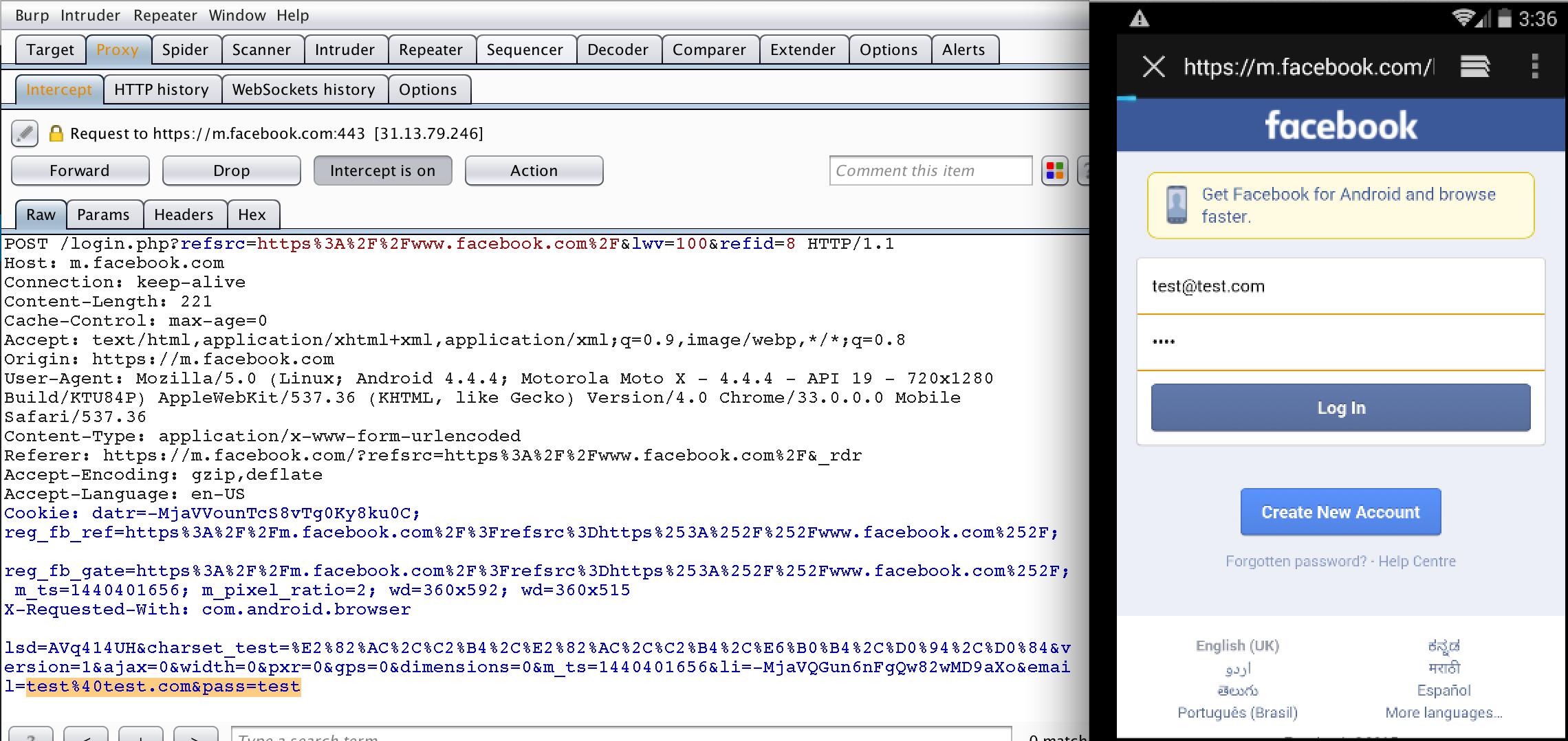
In the intricate world of digital communication, intercepts function as silent gatekeepers, determining how data flows through networks—blocking, redirecting, or mirroring packets with precision. An intercept, in technical terms, is a mechanism embedded within network infrastructure that inspects, captures, and redirects data streams at designated points. Whether in telecommunications, cybersecurity, or enterprise networking, intercepts serve as critical control nodes, enabling traffic management, filtering, and security enforcement.
Far more than passive observers, intercepts actively reshape connectivity, making them foundational to both data protection and strategic network operations.
At its core, an intercept operates by inserting a processing point into the data path between sender and receiver. This insertion allows network systems to analyze packet contents—headers, payloads, headers—before routing decisions are finalized.
“An intercept is where policy meets practice,” explains Dr. Elena Torres, a senior network architect at CyberDefend Solutions. “It’s not just about stopping bad traffic; it’s about intelligently managing what passes through, ensuring efficiency and safety across the entire network.” Transit points known as intercept nodes can range from dedicated hardware appliances to software-based module within firewalls and routers.
Their placement—whether at access points, distribution hubs, or endpoint bridges—directly influences performance and security efficacy.
Types of Intercepts and Their Functional Roles
Intercepts manifest in several forms, each tailored to specific network demands: -Passive Intercepts: Traffic Monitoring Without Interruption
Passive intercepts examine data flows in real time without altering or blocking packets. Utilized extensively in network diagnostics and audit trails, they capture IP addresses, protocols, and timestamps for analysis. These insights support traffic pattern recognition and long-term optimization.> As warned by network expert Martin Cole, “Passive intercepts are the seasoned detectives—they don’t shout, but they gather the evidence that tells the full story of network behavior.” -
Active Intercepts: Enforcing Rules and Redirecting Stream
Active intercepts exert real control by inspecting payloads to apply routing rules, block malicious content, or reroute honest traffic around congestion. Integrated directly into firewalls or reverse proxies, they block threats instantaneously—such as SQL injection attempts or unauthorized data exfiltration—before packets reach their destination. -Mirror Intercepts: Traffic Duplication for Inspection and Testing
Mirror intercepts duplicate network traffic to dedicated monitoring streams.By feeding live data to security tools—discrete from production paths—teams perform deep packet inspection (DPI), forensic analysis, and compliance audits without disrupting service. > “Mirroring transforms a silent relay into an investigative lens,” notes Sarah Lin, lead engineer at SignalTest Labs. “It lets security teams peek behind decisions made by redirectors, revealing vulnerabilities hidden in plain sight.” -
Authenticated Intercepts: Authorized Data Access Control
In secure environments, intercepts verify user or device identity before allowing access.Common in multi-factor authentication gateways, these ensure only privileges-cleared actors process sensitive data, reducing insider threat risks.
Critical Infrastructure and Strategic Adoption
Intercept architecture forms the backbone of secure and efficient modern networks, especially in enterprise, cloud, and telecom settings. In telecommunications, intercept towers and deep packet inspection appliances monitor traffic across 5G networks, filtering spam while enabling QoS—Quality of Service—for critical applications like telemedicine and streaming.Enterprises deploy intercept-based security stacks: intrusion detection systems (IDS), next-generation firewalls (NGFW), and web gateways all integrate intercept modules to enforce shadow IT policies and block advanced persistent threats (APTs). “Corporate networks no longer tolerate blind data flow,” says Dr. Torres.
“Intercepts empower proactive defense, turning passive pipelines into dynamically protected channels.” In cloud environments, intercept layers sit within software-defined networking (SDN) controllers, automating traffic routing and policy enforcement across distributed data centers. Containerized intercept services ease scalability, adapting in real time to surges in workload traffic and emerging threats.
Intercepts are not visible infrastructure—yet their impact is undeniable.
They embody the quiet precision of modern digital control, where raw data is transformed into protected, purposeful flow. From network operators securing enterprise assets to governments monitoring communications, intercepts bridge detection and action with minimal latency and maximum reliability. As cyber threats evolve and bandwidth demands explode, the strategic design and implementation of intercept systems become indispensable.
Far more than technical footnotes, intercepts define how data’ flows become how connectivity itself is safeguarded and optimized. The true essence of an intercept lies in its role as an intelligent gatekeeper—silent, decisive, and essential—controlling not just packets, but the very promise of secure, efficient communication.



Related Post

Unveiling the Taran Noah Smith Net Worth: A Remarkable Financial Journey from Child Str to Entrepreneur

What Does “Iss” Mean on a Driver’s License? The Hidden Code Behind Your Emblem

Ronaldinho Dates Joined: When Football Glamour Met Personal Milestones

Nyou Today Revolutionizes Urban Mobility with AI-Powered Transit App

